Millions of Patient Records at Risk
December 6, 2023Threat-Led Penetration Testing (TLPT) for DORA

In today’s rapidly evolving digital landscape, the financial sector’s reliance on technology has grown exponentially. This dependence, while fostering innovation and efficiency, has also introduced significant vulnerabilities, particularly in the realm of cybersecurity. Recognizing the critical need to bolster the financial system’s resilience against cyber threats, the European Union enacted the Digital Operational Resilience Act (DORA). DORA aims to ensure that financial entities can withstand, respond to, and recover from all types of Information and Communication Technology (ICT)-related disruptions and threats.
A pivotal component of DORA’s comprehensive framework is the implementation of Threat-Led Penetration Testing (TLPT). TLPT is designed to rigorously assess the cybersecurity defenses of financial institutions by simulating real-world cyberattacks. This proactive approach enables organizations to identify and address vulnerabilities before they can be exploited by malicious actors.
Understanding Threat-Led Penetration Testing (TLPT)
Definition and Objectives of TLPT
Threat-Led Penetration Testing (TLPT) is an advanced form of security assessment that emulates the tactics, techniques, and procedures (TTPs) of real-life threat actors. The primary objectives of TLPT are to:
- Evaluate an organization’s ability to detect, respond to, and recover from sophisticated cyberattacks.
- Identify weaknesses within critical live production systems that could be exploited.
- Enhance the overall cybersecurity posture by providing actionable insights derived from simulated attack scenarios.
By conducting TLPT, financial entities gain a realistic understanding of their operational resilience and can implement targeted improvements to mitigate identified risks.
Comparison Between TLPT and Traditional Penetration Testing
While both TLPT and traditional penetration testing aim to uncover security vulnerabilities, they differ in scope, methodology, and objectives:
| Scope | Methodology | Objectives |
| Traditional penetration testing typically focuses on specific applications, systems, or networks, assessing them against known vulnerabilities. In contrast, TLPT encompasses a broader scope, targeting critical business functions and processes to evaluate the organization’s resilience against advanced threat scenarios. | Traditional penetration tests often follow a standardized checklist approach, utilizing automated tools to identify common vulnerabilities. TLPT, however, is intelligence-driven, leveraging current threat intelligence to simulate realistic attack scenarios that mirror the behavior of actual adversaries. | The goal of traditional penetration testing is to identify and remediate technical vulnerabilities within specific systems. TLPT aims to assess the organization’s holistic security posture, including its detection and response capabilities, by challenging people, processes, and technologies through sophisticated attack simulations. |
In essence, TLPT provides a more comprehensive and realistic evaluation of an organization’s defenses, ensuring preparedness against evolving cyber threats.
Importance of TLPT in Identifying Vulnerabilities Through Realistic Attack Simulations
The dynamic nature of the cyber threat landscape necessitates that financial institutions adopt proactive measures to safeguard their operations. TLPT plays a crucial role in this endeavor by:
- Uncovering Hidden Vulnerabilities: By simulating advanced attack scenarios, TLPT can reveal weaknesses that may not be detected through conventional testing methods.
- Assessing Incident Response Capabilities: TLPT evaluates how effectively an organization can detect, respond to, and recover from cyber incidents, providing insights into areas that require enhancement.
- Validating Security Controls: Through realistic attack simulations, TLPT tests the effectiveness of existing security measures, ensuring they function as intended under adversarial conditions.
- Enhancing Organizational Preparedness: By exposing staff to simulated attacks, TLPT fosters a culture of vigilance and continuous improvement, strengthening the organization’s overall resilience.
Incorporating TLPT into the cybersecurity strategy allows financial entities to stay ahead of potential threats, ensuring they are well-equipped to handle real-world cyber challenges.
DORA’s Requirements for TLPT
Overview of DORA’s Mandate on TLPT for Financial Entities
DORA establishes a robust regulatory framework aimed at enhancing the digital operational resilience of financial entities within the European Union. A key aspect of this framework is the requirement for certain financial institutions to conduct Threat-Led Penetration Testing. This mandate underscores the importance of proactive cybersecurity measures in safeguarding the stability and integrity of the financial system.
Criteria for Financial Entities Required to Perform TLPT
Under DORA, the obligation to conduct TLPT applies to financial entities that are deemed critical to the financial system’s stability and are likely targets for cyberattacks. These entities include, but are not limited to:
- Credit institutions (banks)
- Investment firms
- Insurance and reinsurance companies
- Payment service providers
- Electronic money institutions
The determination of whether a financial entity is required to perform TLPT is based on a two-level approach:
- Systemic Importance: Entities whose failure could have systemic implications for the financial sector.
- Risk Exposure: Entities that are highly exposed to ICT risks due to the nature of their operations.
By focusing on these criteria, DORA ensures that the most critical and vulnerable institutions are subject to rigorous testing to enhance their operational resilience.
Frequency and Scope of TLPT as Specified by DORA
DORA mandates that qualifying financial entities conduct TLPT at least once every three years.
TLPT Methodology and Phases
The TLPT process is divided into three primary phases: Preparation, Testing, and Closure.
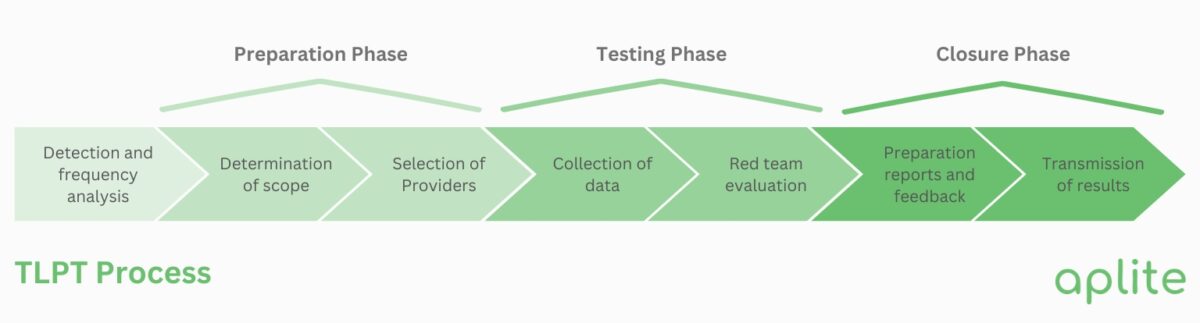
Establishing the Testing Framework and Notifying Relevant Stakeholders
The preparation phase begins with the establishment of a comprehensive testing framework. This involves defining the objectives, scope, and rules of engagement for the TLPT. Key stakeholders, including senior management and relevant departments, are notified to ensure alignment and support. Clear communication channels are established to facilitate coordination throughout the testing process.
Forming the Control Team and Defining the Scope of the Test
A Control Team is assembled, typically comprising members from the organization’s risk management, IT, and compliance departments. This team is responsible for overseeing the TLPT process, managing risks, and ensuring that the test aligns with organizational objectives. The scope of the test is meticulously defined, focusing on critical functions and systems that, if compromised, could significantly impact the organization’s operations.
Gathering Threat Intelligence to Inform Testing Scenarios
In this phase, threat intelligence is gathered to inform the development of realistic attack scenarios. This involves analyzing current threats relevant to the organization’s industry and operations. The goal is to identify potential adversaries, their motivations, and the tactics, techniques, and procedures (TTPs) they might employ. This intelligence forms the basis for crafting scenarios that accurately reflect real-world threats.
Conducting Red Team Testing to Simulate Real-World Attacks
With the threat intelligence in hand, the Red Team—comprising skilled security professionals—conducts simulated attacks on the organization’s live production systems. These simulations are designed to mimic the behavior of actual threat actors, testing the organization’s detection and response capabilities. The Red Team operates covertly to ensure that the organization’s defenses are challenged under realistic conditions.
Analyzing Results and Replaying Actions to Assess Impact
Following the testing phase, the results are thoroughly analyzed. The Red Team compiles a detailed report outlining the vulnerabilities exploited, the success of their attack vectors, and the overall effectiveness of the organization’s defenses. This analysis often includes a replay of the attack scenarios to provide a clear understanding of how the breaches occurred and their potential impact.
Developing Remediation Plans to Address Identified Vulnerabilities
Based on the findings, the organization develops remediation plans to address the identified vulnerabilities. This involves prioritizing the risks, implementing corrective actions, and enhancing security controls to prevent future incidents. The remediation plans are documented and tracked to ensure that all issues are resolved in a timely manner.
Roles and Responsibilities in TLPT
Effective execution of TLPT requires clear delineation of roles and responsibilities among internal teams, external testers, and threat intelligence providers.
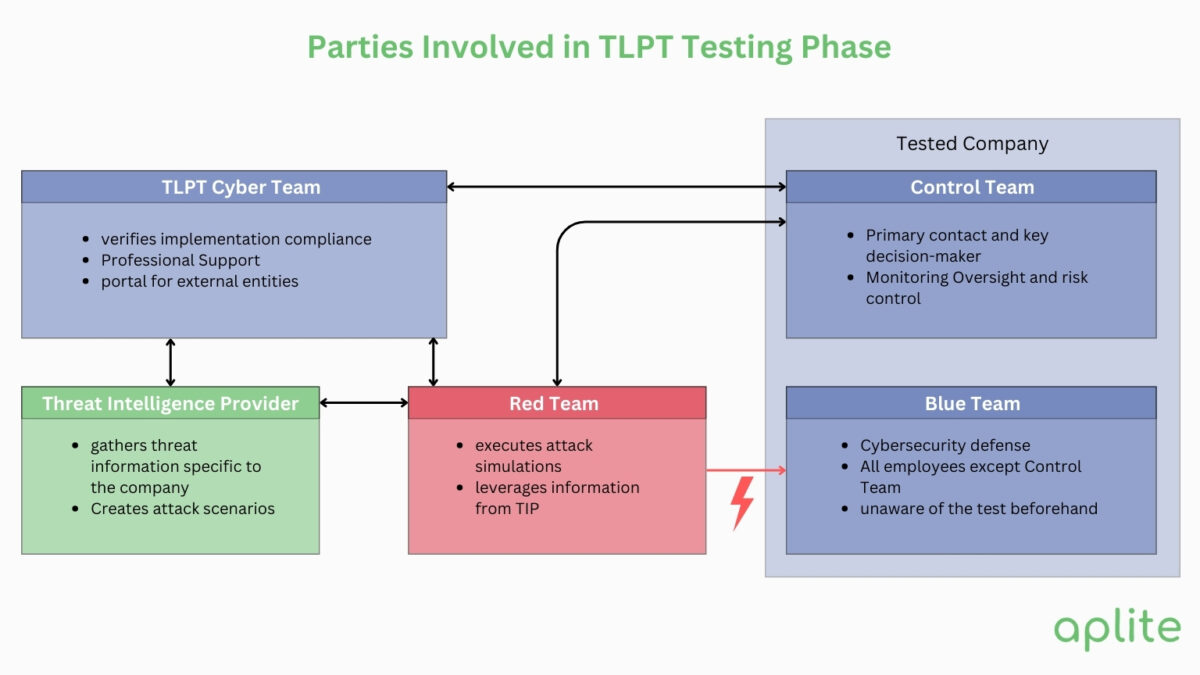
Involvement of Internal Teams (Control Team, Blue Team) and Their Functions
- Control Team: This team oversees the TLPT process, manages communications, and ensures that the testing aligns with organizational objectives. They are responsible for risk management and act as the liaison between internal stakeholders and external testers.
- Blue Team: Comprising the organization’s internal security personnel, the Blue Team is responsible for detecting and responding to security incidents. During TLPT, the Blue Team operates without prior knowledge of the simulated attacks to ensure an unbiased assessment of their capabilities.
Role of External Testers and Threat Intelligence Providers
- External Testers (Red Team): These are third-party security experts engaged to conduct the simulated attacks. They bring an outsider’s perspective, employing advanced techniques to challenge the organization’s defenses. Their independence ensures an objective evaluation of the organization’s security posture.
- Threat Intelligence Providers: Specialists who supply up-to-date information on current threat landscapes. They analyze data to identify potential threats relevant to the organization, enabling the development of realistic and pertinent attack scenarios.
Importance of Collaboration Between Internal and External Parties
Collaboration between internal teams and external parties is crucial for the success of TLPT. Open communication ensures that the testing is comprehensive and that all parties are aligned on objectives and expectations. This partnership facilitates knowledge sharing, enhances the accuracy of threat simulations, and ensures that remediation efforts are effective and comprehensive.
Regulatory Oversight and Compliance
Adherence to regulatory requirements is a fundamental aspect of TLPT, particularly under frameworks like the Digital Operational Resilience Act (DORA).
Process of Documentation and Attestation Post-TLPT
Upon completion of the TLPT, comprehensive documentation is prepared, detailing the methodologies used, findings, and remediation plans. This documentation serves as evidence of the organization’s commitment to cybersecurity and is often required for regulatory compliance. An attestation is typically provided by the external testers, confirming that the TLPT was conducted in accordance with established standards and protocols.
Role of Competent Authorities in Validating TLPT Results
Regulatory bodies or competent authorities may review the TLPT documentation to assess the organization’s compliance with relevant regulations. They evaluate the thoroughness of the testing, the validity of the findings, and the adequacy of the remediation plans. This validation process ensures that organizations maintain a robust cybersecurity posture and adhere to regulatory expectations.
Benefits of Implementing Threat-Led Penetration Testing (TLPT)
Implementing Threat-Led Penetration Testing (TLPT) offers several significant advantages for financial institutions aiming to enhance their cybersecurity posture:
Enhancement of an Organization’s Cybersecurity Posture
By simulating real-world cyberattacks, TLPT provides a comprehensive assessment of an organization’s defenses. This proactive approach allows institutions to identify and remediate vulnerabilities before they can be exploited by malicious actors, thereby strengthening overall security measures.
Improved Detection and Response Capabilities to Cyber Threats
TLPT evaluates an organization’s ability to detect, respond to, and recover from sophisticated cyber threats. Through these realistic simulations, institutions can assess the effectiveness of their incident response protocols and make necessary adjustments to improve resilience against actual attacks.
Strengthening of Trust with Clients and Stakeholders through Demonstrated Resilience
Regularly conducting TLPT demonstrates a financial institution’s commitment to maintaining robust cybersecurity practices. This dedication not only ensures compliance with regulatory frameworks like DORA but also enhances trust among clients, partners, and stakeholders, reassuring them of the institution’s ability to safeguard sensitive information.
Challenges and Considerations
While TLPT offers numerous benefits, financial institutions must navigate certain challenges to ensure effective implementation:
Potential Risks Associated with Conducting TLPT on Live Systems
Executing penetration tests on live production systems carries inherent risks, including the possibility of system disruptions or unintended data exposure. To mitigate these risks, thorough planning, risk assessments, and the establishment of clear protocols are essential. Engaging experienced professionals to conduct the tests can further minimize potential adverse effects.
Managing the Complexity of Coordinating between Multiple Stakeholders
TLPT involves collaboration among various internal teams and external partners, such as threat intelligence providers and regulatory bodies. Coordinating these efforts can be complex, requiring clear communication channels, defined roles and responsibilities, and effective project management to ensure alignment and successful execution.
Ensuring Continuous Improvement and Adaptation to Evolving Threats
The cyber threat landscape is continually evolving, necessitating that organizations regularly update their testing methodologies and security measures. Implementing a culture of continuous improvement, staying informed about emerging threats, and adapting TLPT strategies accordingly are crucial for maintaining robust cybersecurity defenses.
Conclusion
In the context of the Digital Operational Resilience Act (DORA), Threat-Led Penetration Testing (TLPT) emerges as a vital tool for financial institutions striving to enhance their digital resilience. By proactively identifying and addressing vulnerabilities through realistic attack simulations, organizations can significantly bolster their cybersecurity posture. Embracing TLPT not only ensures compliance with regulatory mandates but also fosters trust among clients and stakeholders, affirming the institution’s commitment to safeguarding sensitive information. Financial entities are encouraged to proactively integrate TLPT into their cybersecurity strategies, thereby fortifying their defenses against the ever-evolving landscape of cyber threats.